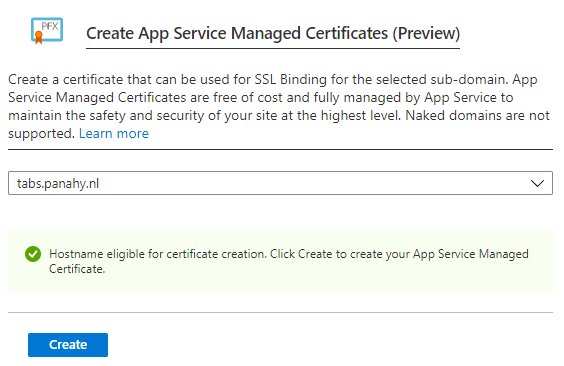
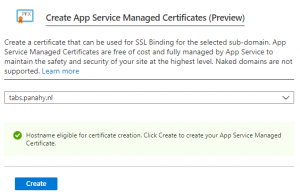
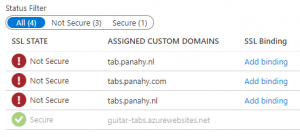
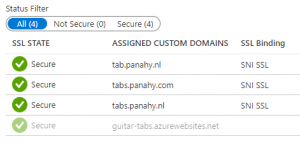
In this page we will create a WebApp that serves a Docker image and see how to put it in CI/CD.
Create a Web App
If you are creating a web app in Azure portal, start with selecting Docker Container as Publish property in Basics tab. Choose Linux as Operating System. For this example a Standard SKU would just do fine.
Next, on the Docker-tab select your existing azurecr.io container registry and specify the Image:Tag you want to serve.
My tempate looks something inline with the following:
"resources": [{
"apiVersion": "2018-11-01",
"name": "[parameters('name')]",
"type": "Microsoft.Web/sites",
"location": "[parameters('location')]",
"tags": {},
"dependsOn": ["[concat('Microsoft.Web/serverfarms/', parameters('hostingPlanName'))]"],
"properties": {
"name": "[parameters('name')]",
"siteConfig": {
"appSettings": [{
"name": "DOCKER_REGISTRY_SERVER_URL",
"value": "[parameters('dockerRegistryUrl')]"
}, {
"name": "DOCKER_REGISTRY_SERVER_USERNAME",
"value": "[parameters('dockerRegistryUsername')]"
}, {
"name": "DOCKER_REGISTRY_SERVER_PASSWORD",
"value": "[parameters('dockerRegistryPassword')]"
}, {
"name": "WEBSITES_ENABLE_APP_SERVICE_STORAGE",
"value": "false"
}
],
"linuxFxVersion": "[parameters('linuxFxVersion')]",
"appCommandLine": "",
"alwaysOn": "[parameters('alwaysOn')]"
},
"serverFarmId": "[concat('/subscriptions/', parameters('subscriptionId'),'/resourcegroups/', parameters('serverFarmResourceGroup'), '/providers/Microsoft.Web/serverfarms/', parameters('hostingPlanName'))]",
"clientAffinityEnabled": false
}
}, {
"apiVersion": "2018-11-01",
"name": "[parameters('hostingPlanName')]",
"type": "Microsoft.Web/serverfarms",
"location": "West Europe",
"kind": "linux",
"tags": {},
"dependsOn": [],
"properties": {
"perSiteScaling": false,
"maximumElasticWorkerCount": 1,
"isSpot": false,
"reserved": true,
"isXenon": false,
"hyperV": false,
"targetWorkerCount": 0,
"targetWorkerSizeId": 0
},
"sku": {
"Tier": "Standard",
"Name": "S1",
"size": "S1",
"family": "S",
"capacity": 1
}
}
As a security matter I have to point out the fact that the Web App is connecting to Azure Container Registry using 3 configuration items i.e. Server Url, Server Username and Server Password. These items are visible in Azure Portal Configuration:
DOCKER_REGISTRY_SERVER_URL, DOCKER_REGISTRY_SERVER_USERNAME, DOCKER_REGISTRY_SERVER_PASSWORD
Deploy Docker Image
In both cases where the Docker image gets pulled from Container Registry, you need to restart the instance in Container Instance and also in Web App Docker instance.
An other option would be to move the pull task into Azure Pipeline using. My example is defined as follows:
steps:
– task: AzureRmWebAppDeployment@4
displayName: ‘Deploy Azure App Service’
inputs:
azureSubscription: ‘$(Parameters.ConnectedServiceName)’
appType: ‘Web App for Containers (Linux)’
WebAppName: ‘$(Parameters.WebAppName)’
DockerNamespace: ‘https://securedcontainerregistry.azurecr.io’
DockerRepository: ‘https://securedcontainerregistry.azurecr.io/securedazurelib’
DockerImageTag: ‘latest’
StartupCommand: ”